Effective protection of companies and data
Those who exchange data with project partners or use Internet services or mobile hardware are taking potential risks. Digital viruses and worms, espionage or hacker attacks can damage hardware and software, disrupt business processes and even paralyze production. So how does one protect company and data against malware, digital sabotage or espionage?
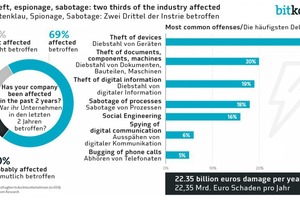
In this digital era, companies are increasingly exposed to digital dangers. In addition to the security problems caused by computer viruses and the careless use of the Internet or mobile hardware, we are seeing a steady increase in espionage and cyber attacks by rival companies or criminals. According to a representative survey conducted by the German IT industry association Bitkom, two thirds of German companies have already been the victims of data theft, industrial espionage or sabotage in the last two years. The damage caused by this is estimated to be around 22.4 billion euros per year. Apart from malware, hacker attacks are increasingly becoming a problem for the IT security of companies in other European countries and overseas. The following article describes the digital threats that can disrupt or even paralyze a company’s manufacturing processes and explains how they can be counteracted.
Security problems caused by malware
Due to the brisk exchange of data in most companies, there are dangers posed by computer viruses that should not be underestimated. Since one deals with many project partners in day-to-day business, there is a high risk of being infected by digital viruses, worms, trojans and other malware. They can encrypt data and make them unreadable, block computers or damage hard drives. So-called bot programs can remotely control PCs without being noticed, while key loggers store and forward keyboard entries. So-called denial-of-service attacks can paralyze networks, phishing websites on the Internet can entice users to disclose sensitive data and much more.
Apart from the exchange of data with project partners, employees can also become a security hole – for example if e-mail attachments from unknown senders are opened, apps or shareware programs are downloaded or private vacation photos are brought along on a USB flash drive for use as wallpaper. Viruses and worms can then lodge themselves in the company network.
The mixing of private and business use of hardware can also become a security problem. The careless handling of text messages, e-mails, app platforms, social networks, etc. can become a problem if a private Smartphone is used for business or vice versa. Once the emergency has occurred and a computer virus has lodged itself in the system files or company hardware, daily business can be impaired to a considerable degree and there could even be a complete loss of production. In many cases hard drives have to be completely reformatted, operating systems and applications reinstalled and configured and all working data reloaded – that’s if any virus-free backup copies are available.
Basic protection for companies and data
How can you protect your office hardware, software and data against these risks? The best protection is offered by several IT security measures that are co-ordinated with one another. They should all ensure the confidentiality, availability and integrity of information and IT systems, avoid damage and minimize risks. This can only be achieved through a package of measures that includes anti-virus programs, firewalls, anti-spam programs, data backup and encryption and data protection.
At the very top of the list of priorities is the anti-virus program: anti-virus programs keep most current malwares at bay – provided the software is kept up to date through regular online updates. So-called firewalls screen a network from external damaging influences. As a rule a firewall consists of hardware and software that control the flow of data between the internal and external networks.
Firewalls are suitable for securing several company PCs. Desktop or personal firewalls serve to protect individual workplace PCs or mobile computers such as notebooks against external attacks. Unlike the network firewall, the personal firewall runs directly on the computer that is to be protected. If, in addition to that, security rules are followed when surfing and sending electronic mail, and the operating system, Internet browser, e-mail program and any application programs are configured for maximum security, then personal firewalls mostly have little to do.
In addition to the security functions already included in the respective operating system, commercial IT security programs from Avira, Kaspersky, Norton, Symantec and others promise even greater security. Basic protection is available from around 50 euros per computer, while relatively good all-round protection can be had for a little more. By the way, security software for business applications differs from versions for private users by the number of installable licenses (minimum five PCs), network functions and other additional services.
The company’s own employees must also be integrated into a comprehensive IT security concept. They can be prevented from becoming a security factor on the one hand by training and security standards. If they understand relationships better they can recognize potential dangers more easily and are more likely to accept security measures that they perceive to be bothersome. However, there is a series of technical possibilities to minimize risks due to careless actions by individuals:
For example, access rights can be defined in the company network to determine who may access which network areas or who may use which applications. Moreover, drives or USB interfaces on individual workstations can be locked. Furthermore, the web server (the computer responsible for the Internet connection) can be configured so that employees cannot access problematic websites. Protection against unauthorized access is offered by a personal user name and biometric control systems such as fingerprint scanners which – installed in keyboards, PC mice, notebooks and so on – are available from retailers.
Integrate mobile hardware
in the security concept too
Mobility is becoming increasingly important in connection with digitization and the local acquisition or presentation of data without media breaks. However, mobile hardware in the form of Smartphones or Tablets, SD cards, USB flash drives or USB hard drives can become a security problem. They are small, light and mobile – and can therefore easily be lost. USB flash drives and SD cards in particular are used for the transportation and exchange of very large quantities of data. But the smaller they are, the greater the danger of losing them when you’re out and about – and thus of sensitive project or company data getting into the wrong hands. You can take precautions by using special transport envelopes or boxes. Protection against hardware theft is offered by special locks with a steel cable, so-called Kensington locks. They are simply inserted into the standard opening and firmly attached to the hardware with a lockable closing mechanism. The lock is usually equipped with a steel cable that allows it to be fastened to objects, for instance a heavy piece of furniture.
If Smartphones, Tablets or USB flash drives should get into the wrong hands, however, a user password or data encryption makes it difficult if not impossible for unauthorized persons to access data. There are now also special protection programs for mobile hardware (e.g. AVG Antivirus free, Lookout, etc.). They keep malware at bay, protect data and in some cases even help to locate lost mobile hardware. They not only protect the hardware against virus infections and harmful apps – they can also prevent mobile devices from becoming virus spreaders the other way round. If the mobile hardware is lost or stolen, its position can sometimes be determined with the help of GPS data.
Data espionage and the consequences
According to the aforementioned survey conducted by the German industry association Bitkom, confidential company data are stolen not only in digital form through hacker attacks over the global data network – in fact, about a third are physically stolen through the theft of data carriers or IT and communication devices such as Smartphones and Tablets. In a further 20 % of cases the espionage takes place through the theft of sensitive digital documents. Acts of sabotage with the objective of disrupting or paralyzing business processes take place to a similar extent in companies. This can lead to losses of time in business processes and it can cause damage to production machinery or reduce product quality. According to the survey, employees are in some cases influenced by various measures to unconsciously disclose confidential information such as passwords. In other companies the electronic communication was intercepted or telephones tapped.
A large portion of the resulting damage is accounted for by losses of revenue due to counterfeits and patent infringements, followed by losses of revenue due to the loss of competitive advantages. Further items are the outlay for procuring replacements for stolen IT and communication data as well as costs due to the downtime of IT systems or the disruption of business processes. Damage to a company’s image as a consequence of security issues should not be underestimated either. What is astounding is that, according to the survey, the company’s own employees are mostly the culprits: current or former employees were responsible for the acts in almost two thirds of the companies affected. One third of the respondents said that the attacks came from the direct periphery of customers, suppliers or service providers. In many cases the culprits from the direct periphery have insider knowledge, which facilitates such crimes. According to the Bitkom survey, competitors were responsible for the acts in 16 % of the respondent companies, while a further 20 % declared that organized groups or foreign secret services were behind the attacks.
What can you do to prevent
IT espionage and sabotage?
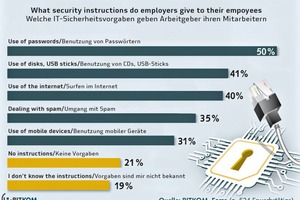
Where technical IT security is concerned, most companies have virus scanners, firewalls and password protection for computers and devices. In view of the many different and increasingly complex threats, however, this common basic protection no longer suffices. Not only that, the networking of machines over the Internet and the trend towards the digital factory (buzzword: “Industry 4.0”) mean that new security challenges have to be overcome. The data-related linking and connection of devices and objects with the Internet multiplies the security weak points in the company. The level of networking is now so far advanced and the relationships so complex that IT attacks often aren’t noticed at all and the leakage of data remains unnoticed over a lengthy period of time. That’s why additional security measures are necessary, such as the encryption of network connections, of data on data carriers or of electronic communication by e-mail. However, only a part of the company does that.
Even less common is the securing of the internal network against the leakage of data from the inside or the use of special attack recognition systems. These systems analyze data streams in a company and report suspicious activities. Further security precautions include advanced methods of user identification, for example a two- or multi-factor authentication. This means that the user is authenticated by means of a combination of two or more different and independent components, for instance by chip card, PIN and in addition the checking of biometric features. Organizational security is increased through rules that determine who can access what data in the internal network and who is given access to sensitive areas of a company. In addition, there should be a security officer who initiates and monitors these measures. An emergency concept worked out together with an IT expert should enable a fast reaction in the event of a crisis.
Conclusion: there is no such thing
as one hundred percent protection!
IT security is important and may even be decisive for the existence of a company – but it’s not easy to obtain. Nowadays, anti-virus software is by no means sufficient and codes of conduct require discipline on everyone’s part.
There is no one hundred percent protection against malware, data espionage, data theft and sabotage. In the constant battle between the malware developers and hackers on one side and the developers of IT security programs and concepts on the other, the former are always one step ahead because of the many different possibilities to cause damage to IT systems. All the providers of IT security solutions can ever do is to react as quickly as possible.
However, the danger potential can be limited to a large extent if the most important security rules are followed and a certain degree of caution and discipline is exercised in dealing with hardware, software, data, e-mails and the Internet.